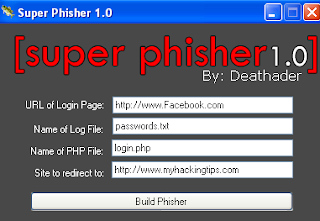
Cellphone is a most popular technology with many good advantages and
different disadvantages. So this is why it came under the list of
hackers. As the popularity is growing more and more, hackers are also
working hard on cellphone hacking. Nowadays 80% off the mobiles are
having Bluetooth installed, which is used for transfering media like
videos, pictures, docs. etc
In this article I would be sharing another good article on Bluetooth hacking. So through my instructions you can control your enemies mobile, when you are in same class or his/her bluetooth is nearer to you and is switched on.

1) Read Messages.In this article I would be sharing another good article on Bluetooth hacking. So through my instructions you can control your enemies mobile, when you are in same class or his/her bluetooth is nearer to you and is switched on.

Some Great Features:-
2) Turn off the phone.
3) Listen Musics.
4) Select modes
5) Block Devices.
6) Contacts
7) Profile Change
8) Ringtone Change
9) Restore Factory Settings.
10) Mobile Restart
11) Volume
12) Make Calls
Easy Installation:-
1) Download It2) Install it on your bluetooth supported device
3) Run it
4) It would restart the device.
5) Choose desired language
6) Choose Connection
7) search devices
8) Select your “victim”
9) Thats it
Now you can hack your victim!Password :- www.saqlainhacking.blogspot.com
Enjoy Hacking.....